Cyber and financial audit

Please use Iphone to browse to:
www.jesperdeboer.nl/quiz.aspx
Agenda
- Own-experience
- Maersk
- Relation with FA
- Frameworks
- Materials you can use
Own-experience
Back in 1996...
Have you ever been hacked?
You should be ok now
Source: https://youtu.be/VaqIYlYmDbA
Annual accounts 2017:
- Cost increased by +- 300 mln
- Effected the result by +- 20%
- Unqualified Opinion
- No key audit matter
Quiz 1: What will you do?
- a. Do nothing
- b. Perform a pentest
- c. Perform a cyber audit based on framework
- d. Reperform client control activities
Results
Relation with Financial audit
- Direct financial damage
- Indirect consequences due to reputational damage
- Loss of intellectual property
- Fines for violating regulations
- Dutch Accounting Standard 400 --> description of the main risks and uncertainties
Our audit approach
DAAM 12200 Internal Control § 146. For audits of listed entities, if we become aware of conditions or events indicating a cyber-security breach, the team shall consult with the NPPD.
Example is
| Incident | Why consultation is required |
| Malware on point of sale systems which resulted in a compromise of credit cards | Significant due to number of stores compromised and potential exposure |
Info and toolkit available: https://techlib.deloitteresources.com?link=content/10006_0901ff81813dbc74
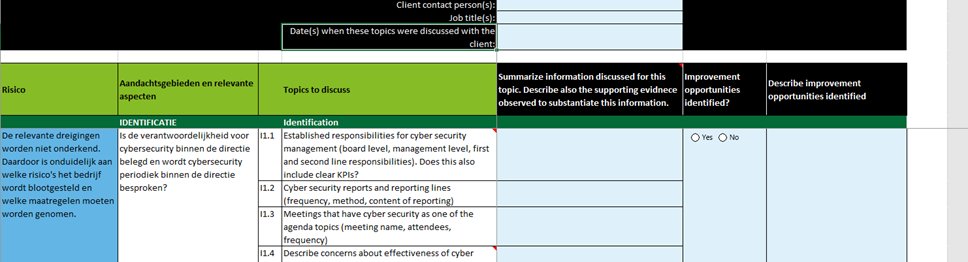
Cyber-frameworks
Deloitte Framework 2018
- Improved and usable "Health check MKB"
- Focus on area’s: identification, prevention, detection, response and recover. We added more focus on governance, responsibilities and vendor management.
- It does not focus on: internal audit and cyber security framework and on technical measures.
- Understand the entity (discussion) or D&I